Photo Credit: telaine via Compfight cc
It was a sunny Saturday afternoon in February and my parents were lending a hand with some decorating. The weather was nice so the rabbit had been released from his hutch and allowed the freedom of the back garden. This was a relatively routine activity and he had not previously displayed any “Great Escape” tendencies.
“Where’s the Rabbit?” – My father enquired.
I initially brushed off the question knowing the rabbit had a habit of hiding behind the shed or the rockery but had always shown up when someone went back into the garden for a few minutes. However, when he failed to turn up half an hour later, I initiated a quick search. This then turned into amore in depth search to the point that I had to pop my head through the open back door to announce “The rabbit is missing!”
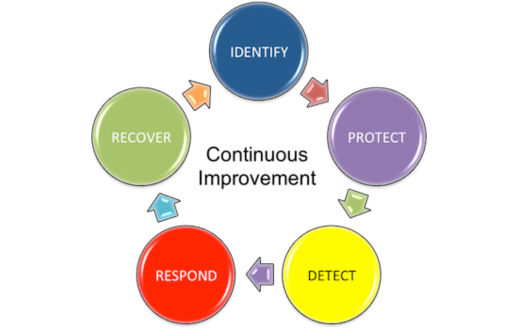
Now, in retrospect I think I probably had applied the first two cyber security principles. I had IDENTIFIED the value of the asset (our rabbit) to the wellbeing of the household and indeed his own needs for a happy and safe life. I thought I had also identified the risks posed by foxes, neighbour’s dogs, birds of prey (yes we do get some in the UK) and our two cats.
I had then PROTECTED him through the use of a sturdy hutch and a run. I had ensured that the fences were too high for him to jump (six foot should do it) with no gaps underneath for him to escape through. In the event that the back gate was to be left open, he would only be able to escape to the front garden, where further fencing provided a physical demilitarized zone. As it was my duty, as designated guard, to provide monitoring services, I thought we had all bases covered. Surely, what else could I have done without defeating the point of having a rabbit in the first place?
So, DETECTION was obviously a bit delayed. The guard (me) was otherwise occupied and did not react to the initial alarm. Once the alert was raised the RESPONSE kicked into gear. We mobilised the incident response team and even called in some of the neighbours. We checked the perimeter, searched the sheds and through the logs – literally. However, as it began to get dark it was becoming clear that the rabbit was gone.
For three days we continued to deal with the shock and sense of loss. Awareness posters were printed and displayed, but with no sign of the rabbit, or how he escaped, we were beginning to accept that this loss might be permanent. Then…after four fraught days he returned.
We are now in a state of RECOVERY. The risks have been re-assessed and the freedom of the rabbit has been severely constrained for the time being.
So, as Information Security professionals, what can we learn from this incident?
As we are beginning to realise that they we may never be able to implement enough controls to completely protect against a reportedly ‘inevitable’ breach, we are starting to direct our efforts increasingly towards detection and reaction. However, we must not forget that all of the principles are equally important in order to fully support our businesses. At the end of the day, we still need to protect the things that are dear to us.
Identifying what is important to the organisation is key to ensuring we focus our limited resources in the right direction and can communicate the threats to a wider community that is increasingly aware, but never the less, confused as to the very real dangers of security breaches.
Protection, whilst seemingly futile, will still limit the opportunities for an incident to occur and many of the controls can support an investigation and any subsequent remediation activities after such an event.
We must have the means to detect a breach of our security controls and an understanding of the impact on the confidentiality or integrity of the information we hold. Our business stakeholders, and most importantly, our customers will expect us to know when an incident occurs and to be able to react instantly.
Reaction must be rapid, but appropriate to the severity of the incident. Support teams and strategic business partners must be able to provide assistance to minimise the effects and protect evidence.
Ultimately the business must be able to recover. Business impact assessments will aid in the understanding of the real criticality of assets, with strong business continuity planning in place to ensure that our businesses can continue to function after a disruption. Further analysis of the cause and effect of a breach must be completed and lessons learned in order to reassess the risks and improve the protection of key assets.
As for my family, we never really understood the value of our asset until it had gone. We may never know what the rabbit got up to during those four missing days and we still don’t know how or if he escaped (or just hid). As the memory of the pain and emotional upset fades, it is likely that the controls will gradually relax and ‘business as usual‘ will resume. We intend to remain more vigilant, but we can’t protect against everything without locking him away for good and that would seriously impede his quality of life and our enjoyment of owning a pet.
The name of the rabbit was not omitted from this article specifically to protect his identity, but for the simple reason that the family never came to agreement on his name and so just address him as “Rabbit”. – Maybe there is another lesson to be learned from that.